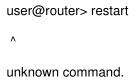
You have a Junos Pulse Secure Access Service acting as an IF-MAP client, configured to fed
A. The Junos Pulse Secure Access Service redirects the user to the Junos Pulse Secure Access Service for authentication
B. The Junos Pulse Access Control Service provisions enforcement points to enable resource access for that user.
C. The Junos Pulse Secure Access Service publishes user session and role information to the IF- MAP Federation server,
D. The Junos Pulse Secure Access Service provisions enforcement points to enable resource access for that user.
 如搜索结果不匹配,请 联系老师 获取答案
如搜索结果不匹配,请 联系老师 获取答案